VMware Server 2.0 Security - Access, Roles and Permissions
| Previous | Table of Contents | Next |
| Command Line Management of VMware Virtual Disks | Controlling VMware Virtual Machines from the Command Line with vmrun |
| Purchase and download the full PDF and ePub editions of this VMware eBook for only $8.99 |

|
Whilst there has been much coverage of the advantages offered by virtualization solutions such as VMware Server, it is only relatively recently that attention has been given to the potential security risks associated with deploying such technology. Whilst the guest operating systems running in virtual machines are, arguably, no less vulnerable than those running on physical hardware (unless the underlying hypervisor itself is in some way compromised), unauthorized access to the virtualization management interface gives an intruder the ability to power off and even permanently delete mission critical systems and data.
The goal of this chapter of VMware Server 2.0 Essentials is to provide an overview of the security access and permissions controls offered by VMware Server 2.0
VMware Server 2.0 Access Controls
The security features of VMware Server are designed to both control access to the VI Web Access management interface, and to restrict the activities that may be performed once a user has successfully logged in.
Access to the VI Web Access interface is controlled by the login screen which is presented when a web browser connects to the VMware Server system. Rather than duplicate functionality, VMware Server leverages the login and password mechanism offered by the host operating system. This level of security works in conjunction with VMware Server specific roles and permissions, defined by an administrator, which govern permitted actions once the user is logged in.
As such, a user can only log into the VI Web Access interface if they have a valid login and password on the system hosting VMware Server 2.0. In addition, the user must have been assigned the appropriate login permissions by a VMware Server administrator (by default, all users on the host system are configured to have no access). The first administrator was created during the VMware Server 2.0 installation process, though other users may be assigned administrative privileges through the VI Web Access interface.
Understanding Privileges, Roles and Permissions
Once a user has successfully logged into the VI Web Access interface, the next level of security involves the use of privileges, roles and permissions to control the actions which the user can perform and the information to which access is permitted.
A privilege provides the right to perform a particular task on a specific VMware Server object within an object category. For example, a user may be given the privilege to power off a virtual machine.
Roles are essentially a number of privileges grouped together and given a name which can then be assigned to users and groups on specific objects or categories. For example, a group of privileges may be bundled into a role for trainee administrators which allows them power virtual machines on and off, but not to remove them from the inventory. VMware Server is supplied with a three pre-defined roles:
- No Access - The default role for users other than the administrator. Denies access to the VI Web Access interface. Attempts to log in will be met with a You do not have permissions to login to the server message.
- Read Only - Allows the user to login and view, but not change, configuration settings and virtual machine states. Access to virtual machine consoles is also denied.
- Administrator - Provides full privileges to all aspects of VMware Server 2.0, including the ability to configure roles, permissions and privileges for all users and groups.
Obviously, a role does very little unless it is applied to a user or group of users and one or more VMware Server object. This pairing is referred to as a permission. For example, assigning the read-only role to a specific user, and applying that to an inventory object is essentially creating a permission.
Creating, Modifying and Removing Roles
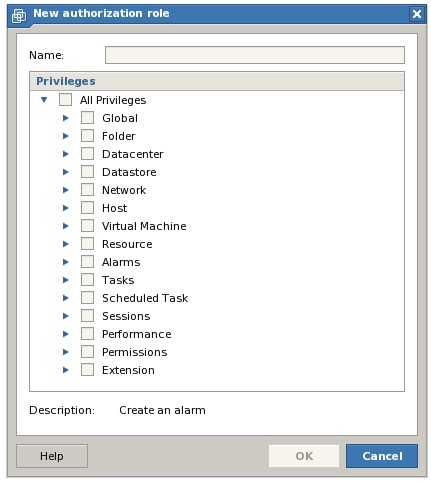
As previously outlined, a role is a collection of privileges brought together in a named group. In addition to the three pre-defined system roles, it is also possible to construct custom roles from a wide range of privileges. To create a custom role, log into the VI Web Access interface as a user with administrative privileges, and select the Administration -> Manage Roles menu option to invoke the Manage Roles dialog. Once displayed, this dialog will list any existing roles. To create a new role, click on the Add button to launch the New Authorization Role dialog as illustrated below:
In the New Authorization Role dialog, enter a name for the new role in the field provided and then construct the role by enabling the required privileges. Note that each category may be selected in its entirety by selecting the category. Alternatively, unfold a category sub-tree and select from individual privileges. When the required privileges have been selected, click on OK to create the new role, at which point the role will appear in the list under the specified name.
To modify a role, select it from the list in the Manage Roles dialog and click on the Modify button. In the Edit existing roles dialog, make the necessary changes to the privilege selections, rename the role if necessary and click on OK to commit the modifications.
An existing role may be removed from the system by selecting it from the Manage Roles dialog and clicking on the Remove button. If the selected role is currently assigned to users or groups a dialog appears provided the choice to remove the role entirely together with any associated permissions, or to re-assign permissions to another pre-existing role.
Creating, Modifying and Removing Permissions
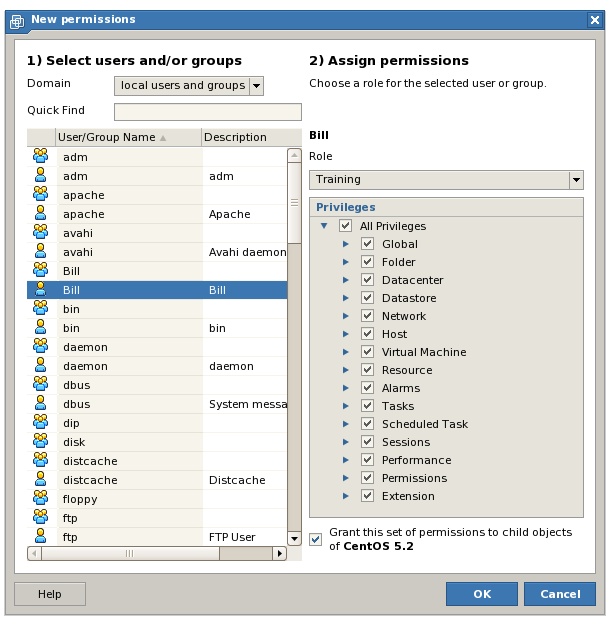
A permission is a combination of a role and a user or group and assigned to a VMware Server object. For example, a custom role called Training applied to a user called Bill and assigned to a virtual machine called win2008 is a permission since it dictates the access permissions Bill has to the 'win2008 virtual machine.
VMware Server permissions are managed from within the VI Web Access interface. When logged in as a user with appropriate administrative privileges, select the host system or virtual machine to which the new permission is to be associated from the Inventory panel. In so doing the first part of the permission, the VMware Server object, has been selected. Click on the Permissions tab in the workspace area to display the current permission configuration for the selected object.
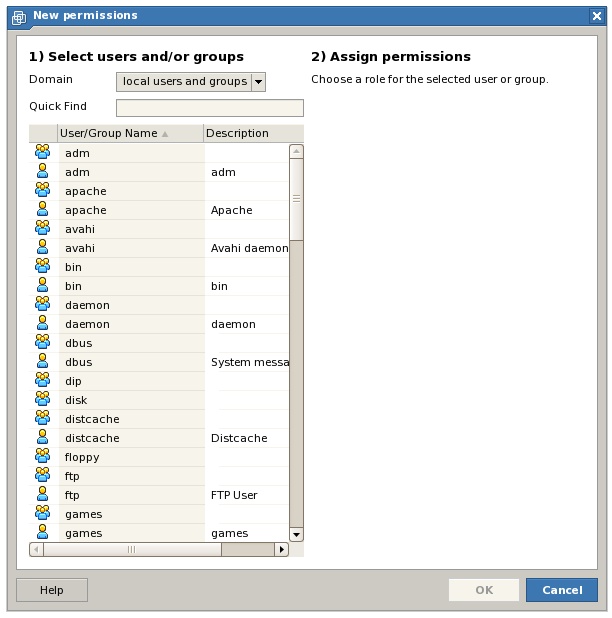
To create a new permission on the selected object, click on the New Permission link located in the Commands panel to invoke the New Permission dialog as shown in the following figure:
From this screen, the second component of the permission is selected, namely the user or group to which the permission is to apply. Once the required user or group has been selected, the dialog updates to provide a drop down menu containing existing roles, together with a list of individual privileges and privilege categories. Either of the options may be used to configure the access privileges for the permission:
To complete the permission creation process, select either a pre-existing role, or select the required combination of privileges. If the permission is to apply to all child objects of the select object, ensure that the Grant this permission to all child objects option is selected. Click OK when completed.
To modify a permission, select the associated host or virtual machine from the Inventory panel, click on the Permissions tab, select the required permission from the list and click the Edit Permission link in the Commands panel. In the Edit Permissions dialog make the changes necessary (including assigning the permission to a different user or group, or associating the permission with a different role) and click on OK to commit the modifications.
To remove a permission, repeat the steps outlined above, selecting the Remove Permission link in place of the Edit Permission link.
| Purchase and download the full PDF and ePub editions of this VMware eBook for only $8.99 |

|